Decentralized Identity - Explained
2022 saw billions wiped off the market, bringing down heavyweights and dominoes — the collapse of FTX and Terra, the bankruptcy of 3AC, Celsius, and Voyager. The infection is far and deep in the wake of FTX, which has been no short of what corona was for the physical world.
Increased attacks, price manipulations, bankruptcies, layoffs, market crashes, and decreased investments mark the crypto calendar of 2022.
The meltdown that has thrown the crypto world into a frenzy is a wake-up call for the users, investors, and all stakeholders.
The FTX crisis has undermined the credibility of the entire crypto ecosystem. But unfortunately, narratives are always misguided, as is the case here. In all of this, essential information and lessons have been missed.
For most of the non-crypto population, the misuse of user funds by FTX is a failure of crypto as a whole. But in reality, it was a failure of centralized control, the exact thing DeFi is trying to change. In fact, with a $40bn+ market cap as of December, DeFi is a promising sector.
The classical failures of FTX, and the plethora of unethical practices, are impossible in an immutable, decentralized, transparent, and permissionless setting of DeFi.
And what is DeFi powered by? Blockchain technology.
Unfortunately, the technology has garnered popularity only in the financial sector (DeFi). But blockchains’ use case extends beyond finance and can secure the democratic process, improve healthcare services, and revolutionize supply chain management, among other social and political applications. The realization of this potential is subject to the creation of decentralized protocols for verifying identity.
Enter Decentralized Identities.
Decentralized Identities
In the simplest terms, it is a digital representation of an entity/individual/device. However, unlike typical identifiers (passports, driving licenses, etc.) Decentralized IDs leverage verifiable credentials (VC) and blockchain to create digital identities that users have control over and can use to log into various systems without exposing their data to online risks.
By design, decentralized identities eliminate dependence on intermediaries (centralized registries, identity providers, or certificate authorities) and protect against identity and data theft.
Why do we need it?
In short, centralized systems suck.
The long version ⬇️
Web3 denotes a future where decentralization is built into the architecture and control is returned from tech behemoths to the rightful owners, i.e., users. The ability of blockchain to deliver on the promise of a future free of intermediaries stems from decentralization.
However, in centralized identity systems, a single entity is responsible for storing all digital data. Digital data encompasses all user (individual, group, or organization) data available online, from photos and emails to physical identity information. E.g., we all use usernames and passwords or OAuth2 to create an account (Facebook, Google, etc.) or to access certain services. In this model, the data is essentially the property of third parties (big tech).
All of our information is housed in siloed databases creating a single point of failure. Additionally, these databases can be compromised through security breaches or centralized attacks. Thus, data tampering/loss, privacy breaches, and cyberattacks are common, raising concerns over the integrity of the systems.
Decentralized identities replace password-based logins with decentralized authentication. They allow for greater control and privacy enabling users to have better control over data. For example, users can selectively share only the necessary information to verify their identity rather than giving broad access to personal information.
Decentralized identity systems return the control and management of data to the users. It is the user’s prerogative to decide how to share the data and with whom.
The setup helps evade the issues that stem from the inherent insecurity of centralized systems and poor cyber hygiene.
Decentralized Identifiers, Verifiable credentials (VC), and blockchain tech are essential elements of Decentralized IDs.
Decentralized Identifiers (DID)
Decentralized identifiers are globally unique identifiers. DIDs enable users (individuals/entities/organizations) to have a cryptographically verifiable, decentralized digital identity. Created and owned by users, DIDs are decoupled from centralized registries and certification authorities.
Verifiable Credentials
Verifiable credentials are a digital representation of physical credentials and digital credentials (with no physical equivalent). VCs, as the name alludes to, are verifiable and respect privacy. The use of digital signatures is the equivalent of the anti-tampering mechanisms on physical credentials, with blockchain enabling instant credential verification.
Blockchain
In contrast to centralized systems, blockchains are more fault-tolerant, attack-resistant, and collusion-resistant. Blockchains provide a global, decentralized, and distributed peer-to-peer network architecture that can tolerate localized shutdowns. All information is publicly accessible to the network participants who are entrusted with validating the legitimacy of the data by utilizing cryptography. Blockchain’s functionality as an immutable digital ledger helps address some of the significant shortcomings of using centralized identity systems: inaccessibility, insecurity, and fraud.
Below is a breakdown of the elements forming part of the decentralized identity setup.
- Issuer — The entity responsible for signing and issuing a Verifiable Credential, writing it in the decentralized ledger, and transmitting it to the holder.
- Holder — Holders are users and owners of the identity. They are the ones that create a DID and receive Verifiable Credentials from the issuer to their wallet.
- Verifier — Refers to the receiver/destination responsible for verifying the authenticity of the VC using the issuer’s DID from the ledger.
- Blockchain/Ledger — Refers to the digital, immutable, decentralized, and distributed ledger that acts as a backbone for decentralized identity systems. It provides the mechanism for DID creation and operation. It serves as a verifiable data registry.
- DID document — Created and owned by users (individual/entity/organization), DID documents describe the Decentralized Identifier (DID). The DID document contains details such as the public key, verification information, and service endpoints to securely authenticate and interact with DID.
- Identity Wallet — A digital wallet that allows the issuer to create and manage their decentralized identity.
Let’s now understand how decentralized identity works with the help of an example.
John wants to apply for a job opening in Firm XYZ. So XYZ requests his educational qualification certificate. Now in Web2, this would entail sharing the soft copy of the original certificate and then XYZ corroborating its authenticity with the issuing authority (University ABC).
In Web3 and with a decentralized identity, John can simply upload his digital certificate on Firm XYZ’s portal. The Decentralized Identifier will authenticate he is the actual recipient.
Alternatively, John (Holder) has a digital certificate that contains a DID. This certificate is signed using a DID that is published and verified by University ABC (Issuer).
XYZ (Verifier) requests John to give permission to view the certificate. At this point, John accepts the request so XYZ can authenticate the digital certificate on the ledger/blockchain.
Basically, the University ABC (Issuer) issues the educational qualification certificate verifiable credential that belongs to John (Holder). Then, ABC and John digitally sign the VC with their respective public keys. The signatures are eventually verified by Firm XYZ (Verifier) to authenticate John as the certificate recipient.
This example demonstrates the kind of application VCs can have in various sectors/businesses. Additionally, they eliminate the possibility of tampering and forgery.
Imagine if you want to rent a house. All you need is proof that you have enough money to pay rent instead of sharing all financial details with the landlord, which is the norm. However, with DID, your bank issues a VC stating you’re in a position to pay the rent (serving as cryptographic proof).
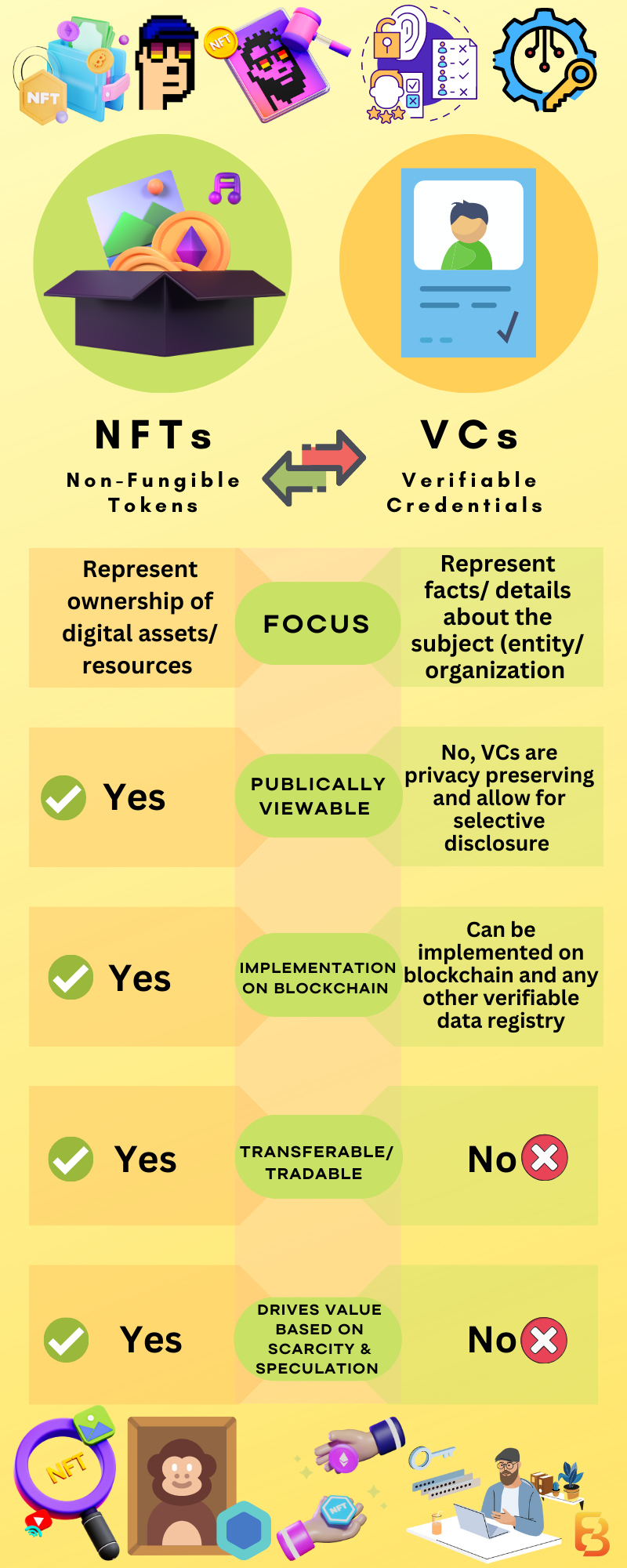
Now, let’s move on to how VCs differ from NFTs because, on the surface, they may seem alike, as they uniquely identify entities in the digital world; however, they differ in their construction and application.
VC vs. NFTS
It’s true that VCs are associated with individuals and can be stored digitally, as is the case with NFTs. However, NFTs represent ownership of digital assets/resources, whereas VCs represent facts/details about the subject (entity/organization/individual).
Moreover, NFTs are associated with public wallet addresses meaning anyone with the address can view the NFTs the user owns or has ever owned. On the other hand, VCs are privacy-preserving and aren’t publicly viewable. However, users can share when required. Furthermore, VCs allow selective disclosure (disclosing only what is needed).
Next, let’s talk about implementation. VCs, as explained above, use public key infrastructure and digital signatures. NFTs are based on blockchain and time-stamped, making the verification process relatively easy. Additionally, any change or transfer in ownership is known and trackable.
Bringing us to transferability. VCs represent the credentials of the holder. So VCs aren’t transferable and can’t be traded; the holder always owns them. NFTs, however, can change ownership.
Last but not least is the element of scarcity. The more scarce the NFT, the greater its value. But for VCs, this is not true as they represent the identity of an entity. Their value is independent of supply and speculation.
I’ll do you one better and explain with a real-world analogy.
An NFT is your ticket to a big event. It essentially grants you access to attend the event. However, you can sell this access (read NFT) to someone else, making NFTs tradeable/transferable. Now, the new owner of the NFT can attend the event.
However, with a VC, the representation is your identity which cannot be sold. Therefore, it represents you exclusively and is issued directly by the appropriate party.
Final thoughts
In today’s data-driven environment, digital identity is essential and must be protected against breaches and leaks. The need of the hour is to gain control over our identities from centralized entities that hold all our information. A decentralized Identity rooted in blockchain can make this a reality.
And while the space is still in its infancy, a lot of progress is being made with innovations like Soulbound tokens, Jack Dorsey’s Web5 (a decentralized data and identity platform leveraging Bitcoin), blockchain biometrics, etc.
If you find this helpful, please support through subscribing and following.
Everythingblockchain 🧐 - Freethinkers, Writers ✍, Blockchain explorers 🔭
In pursuit of simplifying the different blocks of the chain metaverse
Socials
Twitter, Medium, Youtube, Reddit, Substack
Referrals
Braintrust, Presearch, Binance, Kucoin
The information provided through this work is intended solely for educational purposes and must not be treated as investment advice. Any lapses in presenting any of the information correctly are ours alone. We disclaim any liability associated with the use of this content.